Technology Stack
Sending Cryptocurrencies Confidentially
Shielding turns public cryptocurrencies into privacy coins. For example, BTC can be shielded to create pBTC, which retains the value of BTC but can be transacted confidentially. Once shielded, privacy coin transactions are confidential and untraceable.
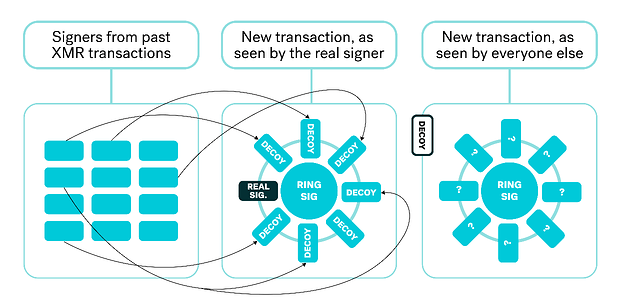
Utilizes linkable ring signature schemes, homomorphic commitment schemes, and zero-knowledge range proofs to shield sending addresses, receiving addresses, and transacted amounts. Fungibility is ensured so that privacy coins are interchangeable and indistinguishable from one another.
A ring signature scheme allows a member of a group to sign a message on behalf of the group without revealing the signer’s identity, preserving anonymity. Linkable ring signatures add a unique identifier to prevent double-spending while maintaining anonymity.


Stealth addresses create unique one-time public keys for each incoming transaction, making it impossible to link transactions to a specific receiver. Based on the Diffie-Hellman key exchange protocol, ensuring that only the intended recipient can recognize and spend the funds.

Confidential Transactions shield the amounts transacted using Pedersen commitments, which include a value and a blinding factor to prevent guessing. Zero-knowledge proofs (specifically Bulletproofs) are used to prove the validity of transactions without revealing amounts, ensuring privacy and preventing inflation.
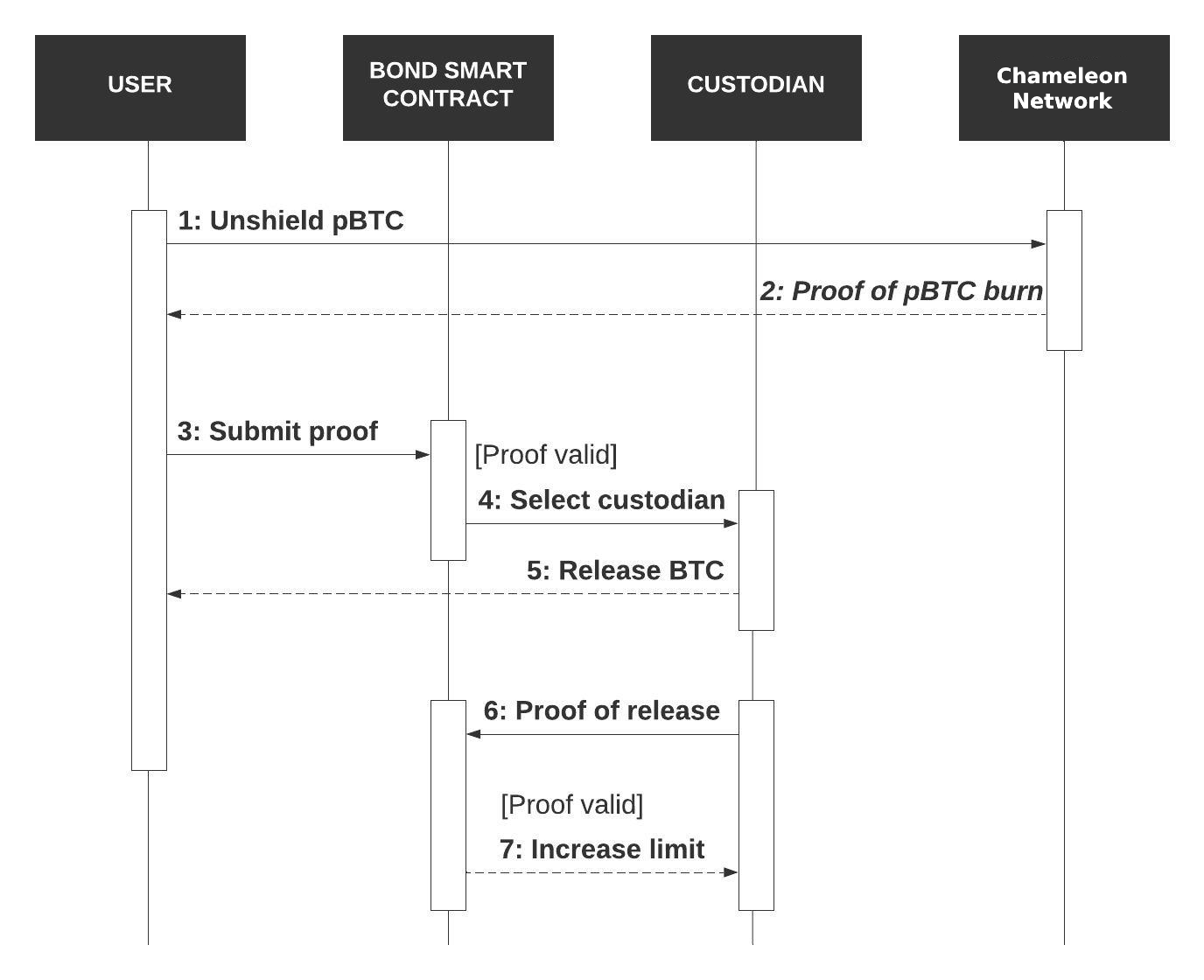
The process of converting privacy coins back into public coins. Involves validators verifying unshield transactions, burning privacy coins, and issuing burn proofs to release public coins at a 1:1 ratio.